Role-based Security Overview
Security is based on roles, which combine tasks and permissions to determine a user access to feature areas. Admins can create roles in one of three ways:
-
Select tasks that appear by default based on the organization's capabilities. For more information, see Manage tasks to provide full access.
-
Customize roles by selecting individual permissions options for tasks, such as View and Add/Edit. For more information, see Permissions.
-
Combine tasks and permissions to determine security. For more information, see Manage tasks and permissions to limit access.
Note: To effectively assign security, it is important to review each topic in this section to fully understand the framework and its impact on your database. It's also important to review roles often to determine whether you need to adjust for new or changed tasks and permissions.
The following diagram displays various security sections. Take note of the feature area on the navigation bar, roles, tasks, and permissions.
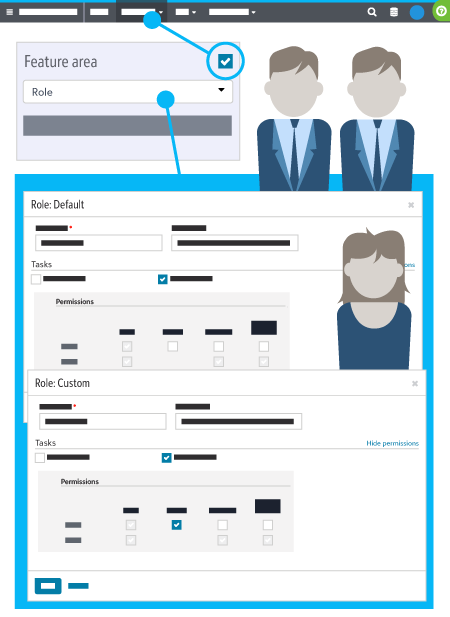
Security preferences persist based on your Blackbaud ID and your browser. For example, if you adjust your preferences in Google Chrome, then you need to adjust your preferences again the next time you log in to Mozilla Firefox. After that, your preferences remain in both browsers.
-
Collapse and expand tiles
-
Moving user detail tiles
-
Moving role tiles and displaying inactive roles
-
Sorting columns
-
Applying filters to lists